Asymmetric cryptography underpins secure communication in the modern digital world. Central to this paradigm are public and private keys, which together form a key pair that enables encryption, decryption, authentication, and non-repudiation. While the public key is openly distributed to anyone wishing to send you encrypted data or verify your digital signatures, the private key remains strictly confidential, granting you exclusive authority to decrypt messages and sign transactions. This guide offers an in-depth look at how these keys are generated, managed, and applied across a variety of real-world contexts—from cryptocurrency wallets to SSL/TLS certificates—and includes detailed best practices for protecting your assets.
1. Fundamental Concepts
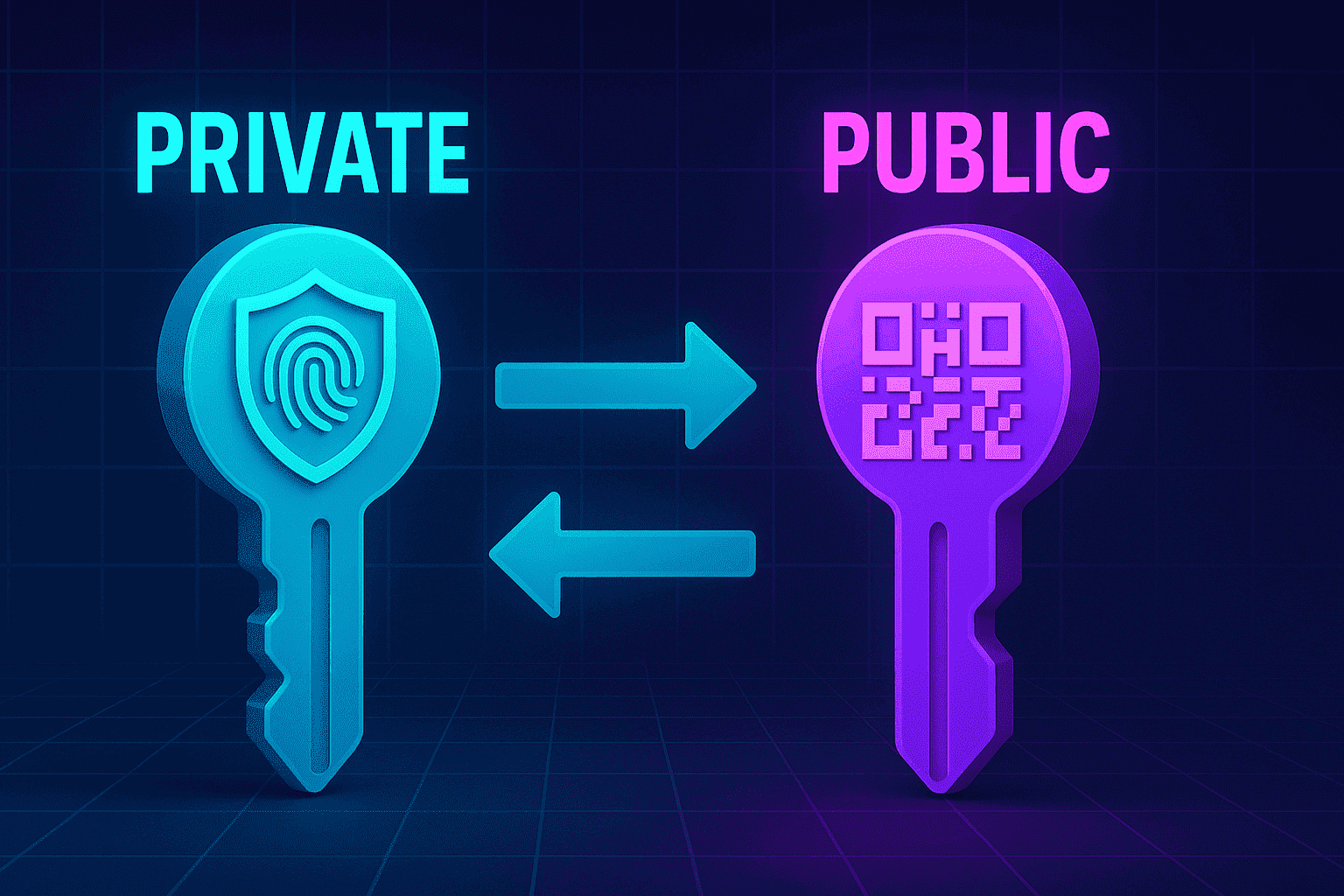
In asymmetric (public-key) cryptography, a key pair consists of a private key and a public key. Mathematically linked, these keys perform complementary functions: anything encrypted with the public key can only be decrypted by the associated private key, and vice versa. This one-way relationship allows you to share your public key widely—anyone can use it to send you confidential data—while your private key remains secret, ensuring that only you can decrypt those messages or generate verifiable digital signatures. Asymmetric cryptography thus delivers confidentiality, integrity, and authenticity without the need for a shared secret channel.
2. The Private Key
2.1 Definition and Role
A private key is a large, randomly generated number—commonly 256 bits in elliptic-curve cryptography (ECC) or up to 4096 bits for RSA—used to decrypt data encrypted with its matching public key and to create digital signatures. Possession of the private key is the ultimate proof of identity: it confirms that you alone authorized a given transaction or message.
2.2 Key Generation
Private keys are generated using cryptographically secure random number generators (CSPRNGs) within trusted software libraries or hardware modules. For ECC, the key is a random integer within the finite field defined by the elliptic curve (e.g., secp256k1). Rigorous entropy collection and seed management ensure that private keys are unpredictable and uniformly distributed across the keyspace, making brute-force attacks computationally infeasible.
2.3 Storage and Protection
- Hardware wallets: Store your private key within a dedicated device isolated from the internet.
- Cold storage: Keep paper or metal backups of mnemonic seed phrases in secure, offline locations.
- Multisignature setups: Distribute control across multiple devices or parties, requiring several keys to authorize high-value operations.
- Secure enclaves: Use trusted execution environments (TEEs) on modern processors to isolate key material from the host OS.
Failing to secure your private key can lead to theft of funds, unauthorized access to encrypted data, or fraudulent signature of transactions. Always follow a strict key-management policy tailored to your threat model.
2.4 Multi-Signature Schemes
A multisig scheme requires M-of-N separate private keys to co-sign a transaction or message. For example, in a 2-of-3 multisig wallet, any two distinct private keys are needed to authorize spending. This enhances security by mitigating single-point failures: even if one key is compromised, an attacker cannot execute transactions without the minimum quorum.
3. The Public Key
3.1 Definition and Properties
The public key is derived from the private key via a one-way mathematical function. It enables others to:
- Encrypt data that only the private key can decrypt.
- Verify digital signatures created by the private key.
Because the derivation is a one-way function, it is computationally infeasible to reverse-engineer the private key from the public key, preserving confidentiality even when the public key is published.
3.2 Distribution and Trust
To prevent man-in-the-middle attacks, public keys are often bound to identity through certificates in a Public Key Infrastructure (PKI). Certificate Authorities (CAs) validate identity documents and issue signed certificates that vouch for the authenticity of a public key. Alternatively, decentralized “web of trust” models allow peers to sign each other’s keys, building trust organically without a central authority.
4. Key Operations
4.1 Encryption and Decryption
When Alice wants to send a confidential message to Bob, she uses Bob’s public key to encrypt the plaintext. The resulting ciphertext travels over any network, but only Bob—holding the matching private key—can decrypt it back to readable form. This process ensures data confidentiality, even if an adversary intercepts the transmission.
4.2 Digital Signatures and Verification
For authentication and integrity, Bob can sign a message by computing a hash and then applying his private key to produce a signature. Anyone with Bob’s public key can verify that the signature matches the message and that it could only have been generated by him. This establishes non-repudiation: Bob cannot later deny having signed that message.
5. Algorithms and Standards
5.1 RSA, ECC, and EdDSA
- RSA: Security relies on the difficulty of factoring large semiprime numbers. Common key sizes range from 2048 to 4096 bits; larger keys yield higher security but also slower computations.
- Elliptic-Curve Cryptography (ECC): Provides equivalent security using much smaller keys (e.g., 256 bits on secp256k1 ≈ 3072-bit RSA). ECC operations are faster and more efficient for modern applications.
- EdDSA (ed25519): A modern signature scheme built on Twisted Edwards curves, offering high performance, simpler implementations, and resistance to side-channel attacks.
5.2 Mnemonic Seed Phrases (BIP-39)
Standards like BIP-39 define how to convert a random entropy value into a human-readable mnemonic phrase (typically 12, 18, or 24 words). This seed phrase can deterministically regenerate the entire hierarchical key structure (HD wallets) for cryptocurrencies, simplifying backups and recovery while maintaining cryptographic security.
6. Practical Applications
- Cryptocurrency wallets: Private keys sign transactions; public keys (or derived addresses) receive funds.
- SSL/TLS certificates: Web servers present signed public-key certificates to browsers, encrypting traffic and verifying server identity.
- PGP/GPG: Email clients use public keys to encrypt messages and verify digital signatures, ensuring end-to-end security.
- SSH authentication: Developers store private keys locally and upload public keys to servers, enabling key-based login without passwords.
- Code signing: Software publishers sign executables with private keys; users verify integrity with the matching public key.
- IoT device authentication: Lightweight key pairs identify and secure communications between edge devices and cloud services.
7. Table 1. Comparison of Private and Public Keys
| Property | Private Key | Public Key |
|---|---|---|
| Primary Function | Decrypt data, create signatures | Encrypt data, verify signatures |
| Distribution | Keep secret (offline storage) | Share freely |
| Generation | Random CSPRNG output | Derived from private key |
| Security Risk | Key compromise leads to total loss | Minimal risk if revoked properly |
8. Table 2. Key Management Checklist
| Step | Action |
|---|---|
| 1 | Generate keys in an offline, secure environment |
| 2 | Store private key in hardware or cold storage |
| 3 | Back up mnemonic seed phrases in multiple locations |
| 4 | Implement multisig for high-value operations |
| 5 | Regularly rotate and revoke old keys |
9. FAQ
- What happens if I lose my private key? Without it, encrypted data and digital assets are irretrievable—always keep secure backups.
- Can I derive my private key from my public key? No—cryptographic algorithms ensure one-way derivation for security.
- How long does signature verification take? Typically milliseconds, depending on hardware and algorithm.
- Are cloud-based key stores secure? They add convenience but introduce additional attack vectors; prefer hardware devices.
- Which is better, RSA or ECC? ECC provides equivalent security with smaller key sizes and faster operations.
- How many words in a seed phrase? Standard lengths are 12, 18, or 24 words under BIP-39.
- What is multisig? A scheme requiring multiple independent key signatures to authorize an action.
- How do I protect against side-channel attacks? Use hardware wallets with built-in countermeasures and constant-time implementations.
- Can I reuse a key for multiple purposes? Best practice is dedicated keys for encryption, signing, and authentication.
- When should I rotate my keys? Regularly, and immediately if a compromise is suspected or after significant personnel changes.
- What is key pinning? Binding a known public key to a service to prevent certificate spoofing.
- How do I revoke a compromised key? Publish a revocation certificate or update your PKI/registry to mark it invalid.
Conclusion
Understanding the interplay between public and private keys is essential for securing digital communications, financial transactions, and software distribution. By following robust key-generation standards, employing secure storage and backup practices, and adopting advanced techniques like multisignature schemes and key rotation, you can significantly reduce the risk of compromise. Whether you’re a blockchain developer, system administrator, or privacy-conscious user, mastering key management will empower you to protect your data and maintain trust in an increasingly interconnected world.